The following is an excerpt from Chapter 3 in the NEW textbook Hacking for Defense, a graduate-level course taught at more than 70 colleges and universities worldwide and on three continents. More than 2,000 students have successfully completed its program.
The Hacking for Defense class requires its students to interview key stakeholders to learn which problem they are solving, which potential solutions might solve them, and how to deliver the solution. These interviews are vital to the students’ success.
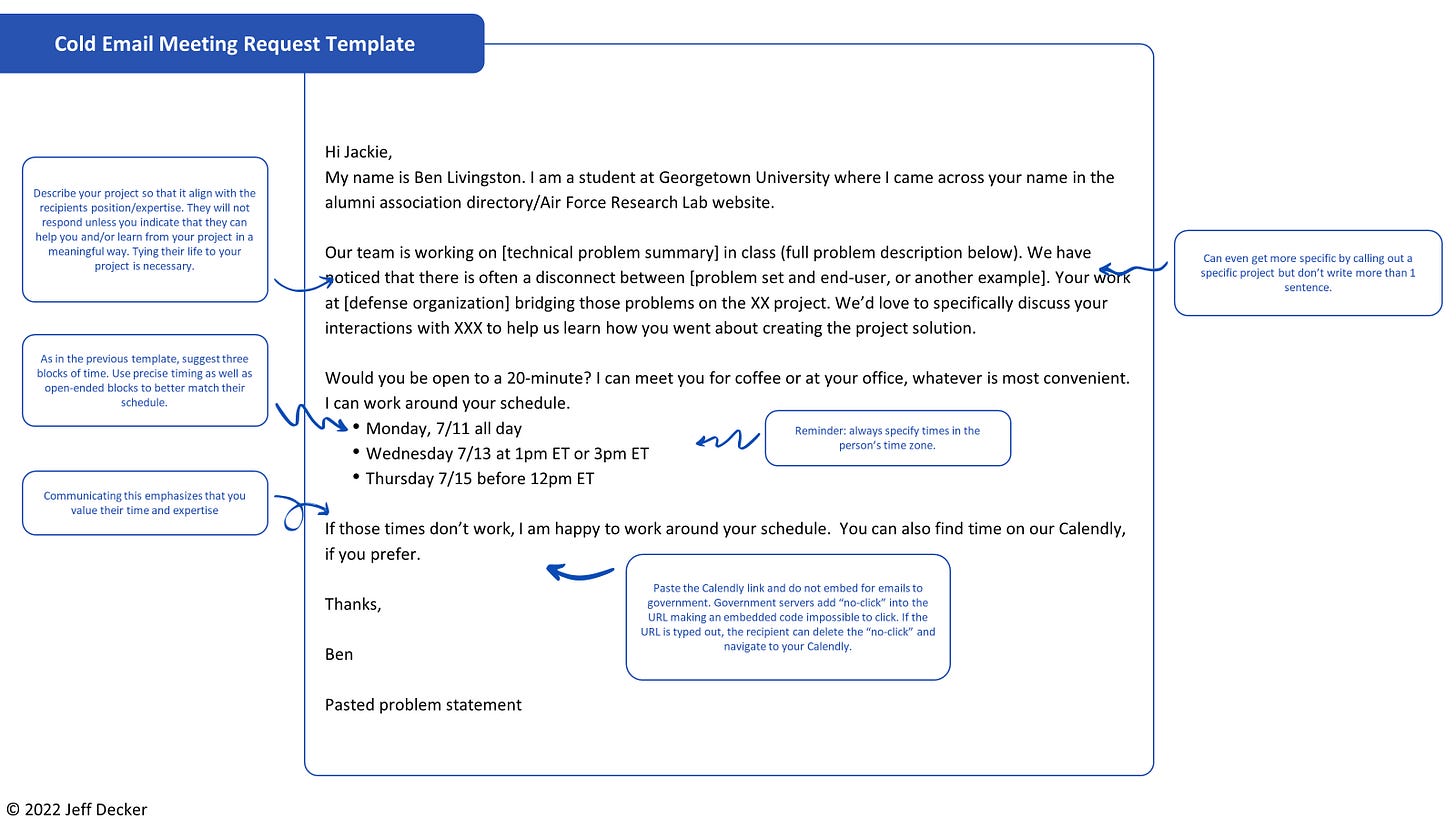
Unfortunately, securing interviews is one of the most time-consuming tasks students will undertake. It is a numbers game. Most outreach fails for two simple reasons: the interview request is unclear and/or the request is overwhelming. This post provides some proven tips and quick and easy email templates to convert more of your interview requests into real interviews.
There are two ways to connect with potential interviewees: cold outreach and warm introductions.
Cold Outreach
Cold outreach is when you request an interview from someone you don’t know and do not have any connection to. You may have found this person through an Internet search or on LinkedIn, or someone mentioned this person but wasn’t able to provide a direct introduction. Put simply, cold outreach is emailing someone out of the blue asking for an interview. This type of interview request has the highest likelihood of failing.
Including the following points in a cold outreach email will increase the likelihood of landing the interview:
State how the contact was discovered and how the person can benefit from being interviewed.
Concisely describe the project and how it relates to the person’s role, experience, or interests. Essentially, the outreach needs to answer their question of, “Why should I take the time to meet with these students?” before they even ask.
Make scheduling easy by suggesting several times, and doing so in the potential interviewee’s time zone.
Emphasize that you are students seeking to learn from them and that you are NOT making contact to sell.
See the below template for an example of what this email might look like.
Warm Introductions
A warm introduction is when students are warmly introduced to the potential interviewee by a third party connection. Warm intros have the highest likelihood of converting into interviews because the person making the introduction is providing their personal endorsement. The primary reason warm introductions fail is that the introducer doesn’t end up making the introduction.
While the introducer might be enthusiastic to connect you to their contact, they may not send the introductory email because drafting a warm intro takes time.The introducer needs to articulate what it is that the students are doing and then relate it to the potential interviewee in a way that emphasizes the importance of them taking the interview.
Hacking for Defense students can ensure the warm email introduction is sent by taking the burden off of the introducer. The below is an email template students can send to the introducer to save the introducer time and increase the likelihood that the warm introduction is made.
Including the following points to a would-be introducer increases the likelihood of them sending the introduction:
In the first sentence to the introducer initial contact, make sure to show some sort of sincere gratitude for their involvement in the work.
Be sure to list the email address and LinkedIn of the potential interviewee contact if you have it. The short note can also be revised to ask if they know anyone at a specific unit or performing a certain job function.
Explicitly state your college/university affiliation.
It is best to specify your availability for the interview date within 10 days so there is some urgency, but not last minute, when asking for a day/time to connect and conduct the interview.
Include the introducer’s email signature block when a real signature [or scanned signature] of the person sending the letter.
As a Hacking for Defense student, there are several resources available to find interviewees and connect to make warm introductions. First, the course problem sponsor is committed to introducing the team to at least 10 contacts. Begin with them. The Hacking for Defense Network, including defense mentors, and others with .mil email addresses, can also be used to make introductions to other military personnel. Students in the class are also valuable resources. Asking if they have interviewed anyone who might be relevant to your problem is a good place to start. In addition to these resources, college/university alumni associations and business mentorship programs, such as SCORE and BENS, can also provide valuable connections to interviewees in the industry.
Most importantly, ALWAYS end an interview with the following question: “Who do you recommend I speak to about this project and can you provide me with an introduction?” This question will lead to additional interviews, referred to as “Snowball Sampling,” that is used to expand the network of potential stakeholders to interview. Try to gain at least two introductions from each interview conducted.
No matter whether you are seeking interviews through cold outreach or warm introductions, be careful to avoid the following:
Don’t overwhelm the contact by sending a long email and/or attachments. You can provide additional information after they have agreed to the interview.
Refrain from embedding links in the email (government computers won’t accept links).
Do not discuss the details of your project if it is sensitive in nature. Rather, provide a high-level description of who your government sponsor and defense mentor are and the problem you are tackling. Where possible, copy your defense mentor and/or government sponsor’s .mil/.gov email address to the email to add credibility.
These tips and templates will save time and increase the chances of successfully connecting with potential interviewees.
Happy interviewing!